The Challenges and Best Practices of Global Firewall Management

Picture this: sales are surging, new offices are popping up in three different time-zones, and every region wants its own slice of the cloud. Life is good—until the security tickets start piling up. Each subsidiary must meet its local privacy law, the help-desk in Sydney wants a rule opened right now, and your night-shift analyst in Dubai is staring at an alert storm that never sleeps. That friction is exactly why the firewall-as-a-service market is on track to reach US $11.41 billion by 2029 with a 28.9 percent CAGR, according to The Business Research Company. More connections and more regulations mean more chances to get burned.
Firewalls in plain English
Think of a firewall as the bouncer who checks every packet’s ID before it walks into the party. You’ll meet four main personalities on today’s guest list:
- Next-Generation Firewalls (NGFWs) – the all-rounders that inspect traffic up to Layer 7.
- Web Application Firewalls (WAFs) – bodyguards for your customer-facing apps.
- Cloud-native firewalls – built into AWS, Azure, GCP, and friends.
- Firewall-as-a-Service (FWaaS) – a fully hosted option that usually lives inside a Secure Access Service Edge (SASE) platform so remote users get the same protection as HQ.
No matter the badge, every firewall enforces policy, blocks bad actors, and keeps a log of what happened just in case lawyers or auditors come calling.
The new security equation when you cross borders
Once you light up that second data center overseas—or even a single SaaS tenant—you inherit three headaches:
- Local laws, global consequences. Rules like the GDPR (EU), PDPL (UAE), or Brazil’s LGPD dictate where data may travel and how quickly you must report a breach.
- An always-on clock. Someone, somewhere, is awake and pushing packets. Maintenance windows now look like a Tetris game across time-zones.
- An expanded attack surface. Multiple clouds, SaaS stacks, and branch offices explode the number of firewalls, consoles, and log streams you must tame.
That’s the IT story. But big enterprises also sit on vast Operational Technology (OT) and Internet of Things (IoT) networks that rarely get the same airtime—and they bring another layer of complexity.
OT and IoT: the fragile half of the network no one wants to patch
Manufacturing lines, power grids, smart meters, and connected trucks run on equipment that was never designed to join the internet. Firewalls in these environments have to contend with:
- Legacy systems that may be a decade old, run out-of-date operating systems, and cannot be patched without shutting down production.
- Proprietary industrial protocols such as Modbus or DNP3—languages most IT firewalls simply don’t speak. Specialised industrial firewalls or deep-packet-inspection cards are essential.
- Zero tolerance for downtime. A sloppy rule change might block marketing’s email server in an office setting, but in a refinery it could stop pumps and trigger a safety incident. Every policy tweak demands a rigorous test plan and a bullet-proof rollback button.
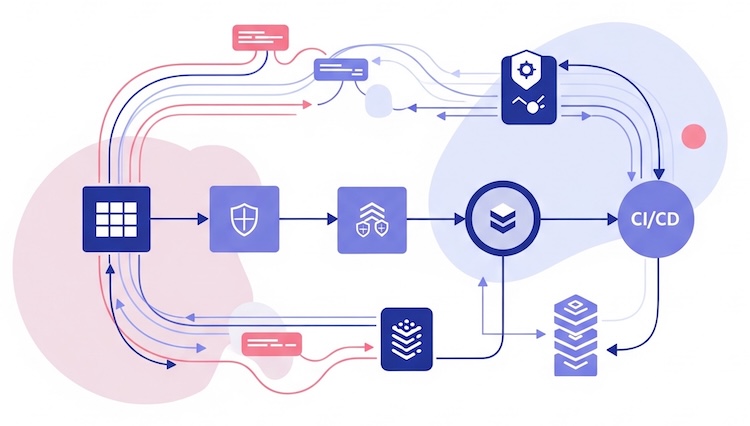
Firewall management meets DevSecOps and Policy-as-Code
The traditional model—submit a ticket, wait three days for approval, deploy the change during a midnight window—collapses when engineers push code to production twenty times a day. Modern teams are moving toward firewall-as-code, where security policies live in the same Git repository as the application:
- Version control & peer review. Every rule sits in a pull request so teammates can spot conflicts early.
- Automated tests in CI/CD. Before code—and its required ports—ever hits production, syntactic and compliance tests run in the pipeline to flag violations.
- Instant rollbacks. If the deployment fails health checks, the pipeline rolls back both the micro-service and its matching firewall rules in one shot.
This approach requires a cultural truce: network security teams must trust developers with policy definitions, and developers must respect the guardrails that keep auditors happy.
Counting the real cost of worldwide firewalls
Security budgets rarely grow as fast as your footprint. Three line items quietly eat cash:
| Cost Driver | Why It Hurts Globally |
| Licensing sprawl | Different regions use different vendors and contract terms, all invoiced in local currency. Tracking renewals is a job in itself. |
| Traffic inspection fees | Cloud firewalls often bill per gigabyte. Send log data from Singapore through a London inspection point and your AWS bill can double overnight. |
| Hidden labor | Training analysts on five consoles, writing multiple runbooks, and staffing follow-the-sun coverage quickly outpaces the hardware cost. |
Smart teams track these costs the same way they track SLA or MTTR—because you can’t fix what you don’t measure.
Supply-chain and third-party risk: your partners’ firewalls matter, too
A modern enterprise may connect to hundreds of suppliers, payment gateways, and logistics APIs. The big challenges:
- Uneven security maturity. That boutique parts supplier in a low-margin industry may run an ancient VPN. You’ll need tighter, more specific rules for them than for a Fortune 500 partner.
- Rule creep. Projects end, but “temporary” firewall exceptions linger for years. Regular audits are critical to delete stale openings before somebody discovers them the hard way.
- High churn. Partner IP ranges, cloud accounts, and connection methods change constantly. Automated inventory and change-detection tools keep documentation and reality in sync.
The regulatory maze at a glance
| Region | Flagship Law | What Your Firewall Must Do |
| EU | GDPR | Keep personal data inside approved zones, encrypt it in transit, and record every access. |
| U.S. (finance) | GLBA, PCI-DSS | Segment card-holder data, run quarterly rule reviews, log everything for a full year. |
| UAE | PDPL | Encrypt personal data flows and notify regulators within 72 hours of a breach. |
| China | CSL & PIPL | Host “critical information infrastructure” onshore, allow periodic deep-packet inspections by state agencies. |
Miss the mark and you risk fines, revoked licences, or an outright service shutdown.
Top challenges for international teams (and how to beat them)
- Conflicting encryption rules. One branch demands export-grade ciphers; the head office insists on FIPS 140-2. Solution: create region-specific decryption zones so traffic never leaves compliance boundaries unencrypted.
- Platform diversity. Palo Alto at HQ, Fortinet in branches, AWS Security Groups for dev, Azure Firewall for analytics. Use a vendor-agnostic Network Security Policy Management (NSPM) tool to push standardised policy objects everywhere.
- Change fatigue. Hundreds of requests a week tempt admins to drop “allow any” rules. Enforce ticket IDs and automatic expiration dates at the API level to keep drift under control.
- Talent shortage. Upskill with role-based training: hands-on command-line labs for engineers, tabletop drills for executives, bite-sized e-learning for branch IT.
- Tool sprawl. Funnel logs and alerts into a single SIEM/SOAR pipeline. One console means faster detection and fewer finger-pointing meetings.
Three pillars of effective global firewall strategy
| Pillar | What to Do | Why It Works |
| Change control & configuration | Standardise a global baseline, then overlay region-specific exceptions. Tie every rule to a ticket that includes a business justification and an expiry date. | Keeps rule sets clean and audit-ready. |
| External connections & compliance | Keep a live inventory of every third-party and partner link. Run automated compliance scans so violations pop up before regulators knock. | Reduces supply-chain risk and late-night fire drills. |
| Time-zone orchestration | Follow-the-sun SOC shifts own windows that match their daylight hours, and a global maintenance calendar blocks overlapping changes. | Eliminates “I thought someone else was watching that” failures. |
Extra tactics that close the gaps
- Zero-trust segmentation – Every user or device must prove its identity and context before packets cross zones.
- Threat-intel-driven blocking – Pull STIX/TAXII feeds and auto-create deny rules at all borders within minutes of a new malware campaign.
- Digital-twin testing – Spin up a virtual copy of your firewall in a sandbox. Push rule changes there first; promote to prod only when automated tests pass.
- One-click rollback – If a change tanks traffic in São Paulo, revert instantly without waking up the Singapore team.
- Quarterly audits – Retire orphaned rules, tighten broad subnets, confirm logs still stream into the SIEM, and measure how many findings were closed since the last review.
- Automation everywhere – Script policy pushes, expiry reminders, and drift detection so humans focus on strategy, not syntax.
Metrics that tell you you’re winning
- Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) for each region.
- Rule-change success rate. How often you deploy without an outage or rollback.
- Audit pass score. Track “high-risk” findings closed per quarter.
- False-positive rate. Nobody loves a firewall that blocks real customers. Fewer false alarms keeps business units on your side.
- Cost per inspected gigabyte. Visibility into traffic spend prevents month-end sticker shock.
Emerging tech to watch
- AI-guided policy suggestions. Natural-language analysis of logs spots redundant or risky rules you missed.
- SASE convergence. Edge points of presence (POPs) embed firewall logic for low-latency filtering wherever your users roam.
- Post-quantum crypto. Start testing quantum-safe algorithms for VPNs before the curve catches up.
Bringing it all together
Picture global firewall management like guiding jets through busy skies, not stacking bricks. You need rules everyone can read, automation that moves as fast as the cloud, and pros who speak both packet-talk and local law. Layer those tactics, watch the numbers that count, and tune the process each quarter. Soon enough, far-flung networks start acting like one tough, well-synced shield.
Get the mindset right, roll out the right gear, and your crew will keep data safe, keep regulators calm, and keep growth rolling—no matter how many time zones, robots, smart meters, or SaaS apps pile on.